Code Safe.
Ship Safer.
Citadelis Decentralized Cyber Defense for a Connected World
Your security layer, powered by global threat data and verified on-chain.
Join the NetworkIn today's hybrid cloud and Web3 environments, centralized security tools are outdated, reactive, and blind to evolving threats.
lost to exploits in 2024
of breaches could’ve been stopped with early detection
of Web3 protocols use real-time defense
the average time to discover a vulnerability
Citadelis solves this with decentralized threat mapping and edge-secured validation.

Real-World Infrastructure. Distributed. Verifiable.
Citadelis is a decentralized cybersecurity mesh where every node contributes to threat detection, validation, and prevention.
Each node delivers:
Citadelis is a decentralized cybersecurity mesh where every node contributes to threat detection, validation, and prevention.
At the core of Citadelis is $CITA, a purpose-built token that anchors the entire defense ecosystem. It reinforces trust, secures operations, and powers every layer of protection.
What Sets Citadelis Apart
Central control points that can be compromised
Delayed updates and reactive fixes
Opaque decision-making and hidden data
Limited scope of protection
$CITA
Distributed architecture with no single failure point
Real-time, autonomous threat mitigation
Transparent, verifiable defense records
Network-wide coverage with adaptive response
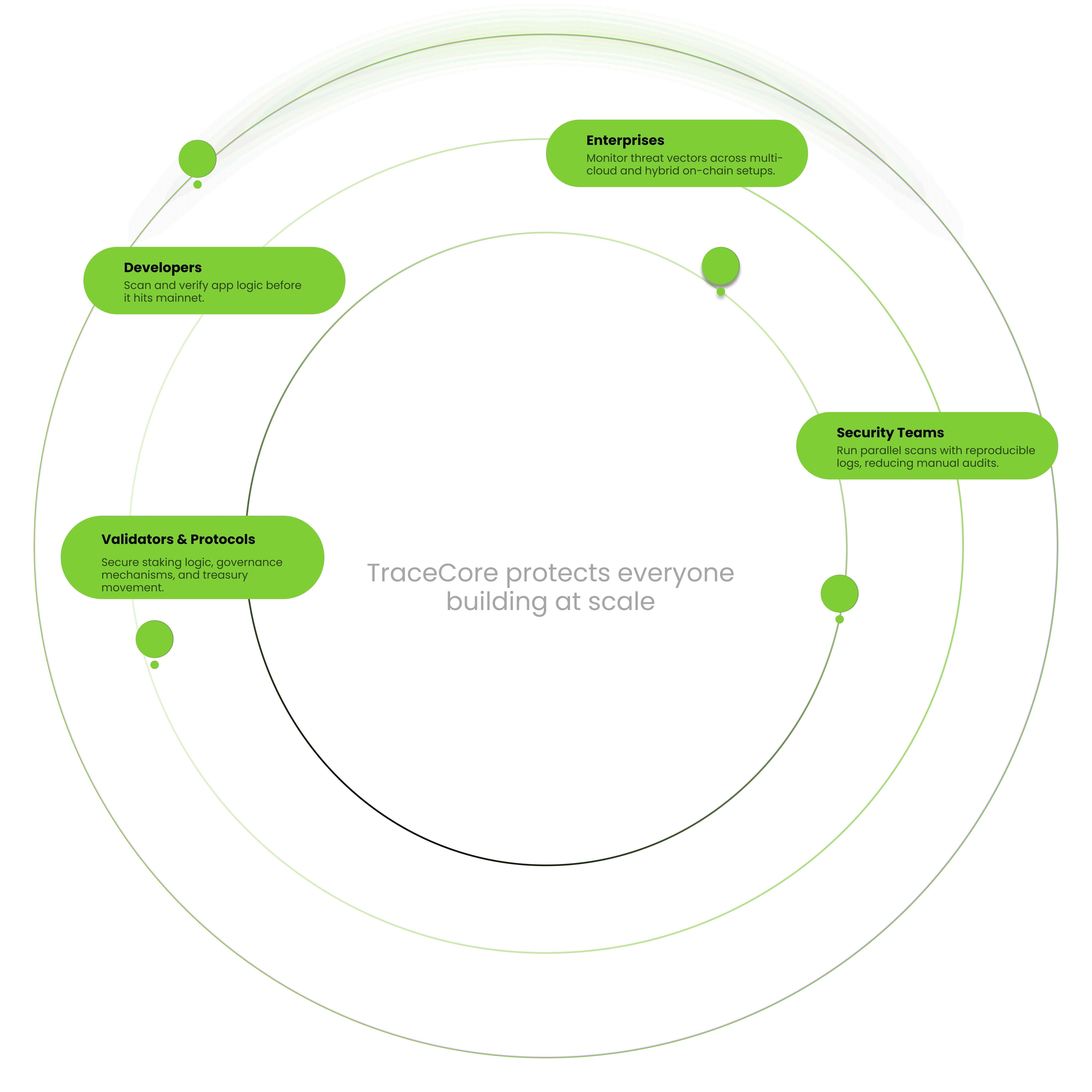
From Local to Global Defense in Three Layers
Distributed scanning agents run threat tests on smart contracts, APIs, and endpoints.
Results are verified via peer consensus across the network. Risk scores and patch suggestions are timestamped on-chain.
Verified threats are logged into a shared registry. Every connected app and infra component can pull the latest defense data instantly.
Every scan, update, and breach prevention is verified.
Citadelis logs every security interaction immutably.